完全に言い訳なのですが、Trivyの検証ブログをなかなか書けず。。。
そして!
書いた?
[DigitalOcean]KubernetesでWordPressを動かしてwikiブログを始めました! https://t.co/kum6pU11vA
— adachin?SRE (@adachin0817) August 13, 2019
k8sを先月から運用し始めたので、コンテナの脆弱性をスキャンしようと、ようやくTrivyの検証をしてみたのでブログします!
■Trivyとは
https://github.com/aquasecurity/trivy
Vulsはsshで対象のサーバ(Linux)の脆弱性をスキャンできるツール(v0.9.0からAlpineのイメージもスキャン可能)ですが、Trivyはコンテナの脆弱性スキャンをできるツールで、CI環境にも組み込めるOSSです。作者は元フューチャーアーキテクトの@knqyf263 氏!Vuls Serverとかも作っています。(以下スライドより)
他のコンテナスキャンツールとの比較は以下ですが圧倒的!!スキャン対象OSも紹介します。
- Comparison with other scanners
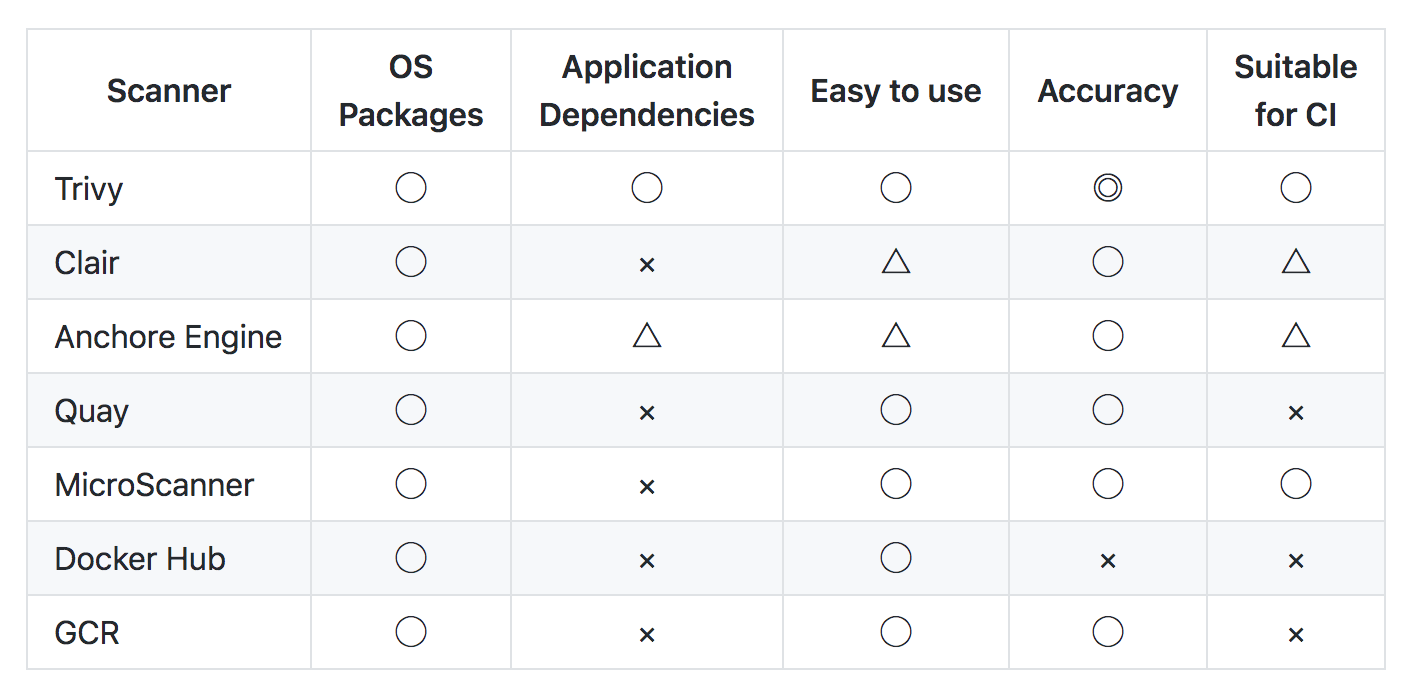
- Alpine Linux (2.2 – 2.7, 3.0 – 3.10)
- Red Hat Universal Base Image (7,8)
- Red Hat Enterprise Linux (6,7,8)
- CentOS (6,7)
- Debian (wheezy, jessie, stretch, buster)
- Ubuntu (12.04, 14.04, 16.04, 18.04, 18.10, 19.04)
AmazonLinuxは対応していません!早速 wiki.adachin.me で動いてるコンテナらをスキャンしてみましょう!ちなみにTrivyの想いとかそこらへんの話も以下に貼っときます!
おおおお!!!この前Vuls祭りでお話してたけど、k8s運用し始めたから今週には検証ブログ書こう?
趣味で作ったソフトウェアが海外企業に買われるまでの話 – knqyf263's blog https://t.co/2nORhXlhzX
— adachin?SRE (@adachin0817) August 20, 2019
■Install
- CentOS/RedHat
|
1 2 3 4 |
$ yum remove trivy $ sed -i s/knqyf263/aquasecurity/g /etc/yum.repos.d/trivy.repo $ yum update $ yum install trivy |
- Debian/Ubuntu
|
1 2 3 4 |
$ apt-get remove --purge trivy $ sed -i s/knqyf263/aquasecurity/g /etc/apt/sources.list.d/trivy.list $ apt-get update $ apt-get install trivy |
- Homebrew
|
1 2 3 |
$ brew uninstall --force trivy $ brew untap knqyf263/trivy $ brew install aquasecurity/trivy/trivy |
今回はMacにインストールしてみました。
- Usage
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 |
NAME: trivy - A simple and comprehensive vulnerability scanner for containers USAGE: trivy [options] image_name VERSION: 0.1.6 OPTIONS: --format value, -f value format (table, json) (default: "table") --input value, -i value input file path instead of image name --severity value, -s value severities of vulnerabilities to be displayed (comma separated) (default: "UNKNOWN,LOW,MEDIUM,HIGH,CRITICAL") --output value, -o value output file name --exit-code value Exit code when vulnerabilities were found (default: 0) --skip-update skip db update --only-update value update db only specified distribution (comma separated) --reset remove all caches and database --clear-cache, -c clear image caches --quiet, -q suppress progress bar and log output --no-progress suppress progress bar --ignore-unfixed display only fixed vulnerabilities --refresh refresh DB (usually used after version update of trivy) --auto-refresh refresh DB automatically when updating version of trivy --debug, -d debug mode --vuln-type value comma-separated list of vulnerability types (os,library) (default: "os,library") --cache-dir value cache directory (default: "/path/to/cache") --help, -h show help --version, -v print the version |
■Scan
- refresh db
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 |
$ trivy wordpress:5-php7.1-apache 2019-09-11T18:07:57.978+0900 FATAL Detected version update of trivy. Please try again with --refresh or --auto-refresh option adachin@lancersMac > trivy --refresh 2019-09-11T18:08:02.633+0900 INFO Refreshing DB... 2019-09-11T18:08:02.656+0900 INFO Updating vulnerability database... 2019-09-11T18:16:35.394+0900 INFO Updating nvd data... 128484 / 128484 [============================================================================================================================================================================================================================================] 100.00% 12m44s 2019-09-11T18:29:19.823+0900 INFO Updating alpine data... 13595 / 13595 [=================================================================================================================================================================================================================================================] 100.00% 43s 2019-09-11T18:30:03.170+0900 INFO Updating redhat data... 19998 / 19998 [===============================================================================================================================================================================================================================================] 100.00% 1m20s 2019-09-11T18:31:23.493+0900 INFO Updating debian data... 29124 / 29124 [================================================================================================================================================================================================================================================] 100.00% 1m1s 2019-09-11T18:32:24.955+0900 INFO Updating debian-oval data... 62012 / 62012 [===============================================================================================================================================================================================================================================] 100.00% 1m28s 2019-09-11T18:33:53.287+0900 INFO Updating ubuntu data... 31254 / 31254 [===============================================================================================================================================================================================================================================] 100.00% 2m22s |
久々にスキャンということもあって、脆弱性データベースをアップデートします。20分かかりました。(これは長い)
- trivy scan
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 |
$ trivy wordpress:5-php7.1-apache 2019-09-11T18:36:24.228+0900 INFO Updating vulnerability database... 2019-09-11T18:36:35.537+0900 INFO Updating ubuntu data... 5 / 5 [==========================================================================================================================================================================================================================================================] 100.00% 0s 2019-09-11T18:36:35.759+0900 INFO Updating nvd data... 13 / 13 [========================================================================================================================================================================================================================================================] 100.00% 2s 2019-09-11T18:36:37.970+0900 INFO Updating alpine data... 6 / 6 [==========================================================================================================================================================================================================================================================] 100.00% 0s 2019-09-11T18:36:38.422+0900 INFO Updating redhat data... 11 / 11 [========================================================================================================================================================================================================================================================] 100.00% 0s 2019-09-11T18:36:38.893+0900 INFO Updating debian data... 19 / 19 [========================================================================================================================================================================================================================================================] 100.00% 0s 2019-09-11T18:36:39.247+0900 INFO Updating debian-oval data... 1417 / 1417 [====================================================================================================================================================================================================================================================] 100.00% 1s 2019-09-11T18:37:32.937+0900 INFO Detecting Debian vulnerabilities... 2019-09-11T18:37:32.998+0900 INFO Updating npm Security DB... 2019-09-11T18:37:41.221+0900 INFO Detecting npm vulnerabilities... wordpress:5-php7.1-apache (debian 10.0) ======================================= Total: 629 (UNKNOWN: 14, LOW: 61, MEDIUM: 495, HIGH: 55, CRITICAL: 4) +---------------------------+---------------------+----------+----------------------+-----------------------+--------------------------------------------------------------+ | LIBRARY | VULNERABILITY ID | SEVERITY | INSTALLED VERSION | FIXED VERSION | TITLE | +---------------------------+---------------------+----------+----------------------+-----------------------+--------------------------------------------------------------+ | apache2 | CVE-2007-0086 | HIGH | 2.4.38-3 | | ** DISPUTED ** The Apache | | | | | | | HTTP Server, when accessed | | | | | | | through a... | + +---------------------+ + +-----------------------+--------------------------------------------------------------+ | | CVE-2019-9517 | | | 2.4.38-3+deb10u1 | HTTP/2: request for large | | | | | | | response leads to denial of | | | | | | | service | + +---------------------+----------+ +-----------------------+--------------------------------------------------------------+ | | CVE-2003-1580 | MEDIUM | | | The Apache HTTP Server 2.0.44, | | | | | | | when DNS resolution is enabled | | | | | | | for client... | + +---------------------+ + +-----------------------+--------------------------------------------------------------+ | | CVE-2019-10082 | | | 2.4.38-3+deb10u1 | httpd: read-after-free in h2 | | | | | | | connection shutdown | + +---------------------+ + + +--------------------------------------------------------------+ | | CVE-2019-10092 | | | | httpd: limited cross-site | | | | | | | scripting in mod_proxy error | | | | | | | page | + +---------------------+ + +-----------------------+--------------------------------------------------------------+ | | CVE-2007-1743 | | | | suexec in Apache HTTP Server | | | | | | | (httpd) 2.2.3 does not verify | | | | | | | combinations of... | + +---------------------+ + +-----------------------+--------------------------------------------------------------+ | | CVE-2019-10081 | | | 2.4.38-3+deb10u1 | httpd: memory corruption on | | | | | | | early pushes | + +---------------------+ + +-----------------------+--------------------------------------------------------------+ | | CVE-2008-0455 | | | | CVE-2012-2687 CVE-2008-0455 | | | | | | | httpd: mod_negotiation XSS | | | | | | | via untrusted file names in | | | | | | | directories with... | + +---------------------+ + +-----------------------+--------------------------------------------------------------+ | | CVE-2007-3303 | | | | Apache httpd 2.0.59 and 2.2.4, | | | | | | | with the Prefork MPM module, | | | | | | | allows local... | + +---------------------+ + +-----------------------+--------------------------------------------------------------+ | | CVE-2019-10097 | | | 2.4.38-3+deb10u1 | httpd: null-pointer | | | | | | | dereference in mod_remoteip | + +---------------------+ + +-----------------------+--------------------------------------------------------------+ | | CVE-2003-1307 | | | | ** DISPUTED ** The mod_php | | | | | | | module for the Apache HTTP | | | | | | | Server... | + +---------------------+----------+ +-----------------------+--------------------------------------------------------------+ | | CVE-2019-10098 | LOW | | 2.4.38-3+deb10u1 | httpd: mod_rewrite potential | | | | | | | open redirect | + +---------------------+ + +-----------------------+--------------------------------------------------------------+ | | CVE-2003-1581 | | | | httpd: Injection of arbitrary | | | | | | | text into log files when DNS | | | | | | | resolution is... | + +---------------------+ + +-----------------------+--------------------------------------------------------------+ | | CVE-2001-1534 | | | | mod_usertrack in Apache 1.3.11 | | | | | | | through 1.3.20 generates | | | | | | | session ID's using predictable | | | | | | | information... | + +---------------------+ + +-----------------------+--------------------------------------------------------------+ | | CVE-2008-0456 | | | | httpd: mod_negotiation CRLF | | | | | | | injection via untrusted file | | | | | | | names in directories with | | | | | | | MultiViews... | +---------------------------+---------------------+----------+ +-----------------------+--------------------------------------------------------------+ ~省略~ |
Total: 629 (UNKNOWN: 14, LOW: 61, MEDIUM: 495, HIGH: 55, CRITICAL: 4)
これはオワッタ…..
近々Dockerfile作ってAlpineで動かそうとしているから問題ないぜ!!(白目)
■Continuous Integration (CI)
https://github.com/aquasecurity/trivy#continuous-integration-ci
CIに組み込みたい場合は脆弱性が存在する場合に終了コードが0で返ってくるので、 --exit-code を入れると脆弱性が存在した場合に1を返すようにできます。CircleCIの場合は以下を参考に。
|
1 2 3 4 5 |
$ trivy --exit-code 1 --auto-refresh -c -q wordpress:5-php7.1-apache ~省略~ Total: 629 (UNKNOWN: 14, LOW: 61, MEDIUM: 495, HIGH: 55, CRITICAL: 4) 1 →これな |
- CircleCI
https://circleci.com/gh/aquasecurity/trivy-ci-test
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 |
$ cat .circleci/config.yml jobs: build: docker: - image: docker:18.09-git steps: - checkout - setup_remote_docker - restore_cache: key: vulnerability-db - run: name: Build image command: docker build -t trivy-ci-test:${CIRCLE_SHA1} . - run: name: Install trivy command: | apk add --update curl VERSION=$( curl --silent "https://api.github.com/repos/aquasecurity/trivy/releases/latest" | \ grep '"tag_name":' | \ sed -E 's/.*"v([^"]+)".*/\1/' ) wget https://github.com/aquasecurity/trivy/releases/download/v${VERSION}/trivy_${VERSION}_Linux-64bit.tar.gz tar zxvf trivy_${VERSION}_Linux-64bit.tar.gz mv trivy /usr/local/bin - run: name: Scan the local image with trivy command: trivy --exit-code 0 --no-progress --auto-refresh trivy-ci-test:${CIRCLE_SHA1} - save_cache: key: vulnerability-db paths: - $HOME/.cache/trivy workflows: version: 2 release: jobs: - build |
■まとめ
そもそもコンテナということもあって、CI環境を連携できるように作られているので、本番コンテナ運用している方にとって重宝しそうです!自分もCircleCI使って活用してみます!



0件のコメント