WordPressの脆弱性ってmajide恐ろしいですよね?サーバに詳しくない人が運用するとすぐ乗っ取られましたとか…そもそもWordPressの脆弱性をスキャンしてくれるサービスやOSSってなかなかない!
そこで!!
wpscanは内部からのスキャンだけど、外から叩くタイプのwordpress脆弱性スキャナ TODOhttps://t.co/ukVrOCAxHe
— ちょんまげ (@kotakanbe) October 16, 2018
神戸さんがこんなツイートをシェアしてたので早速試してみました。(はやっ)
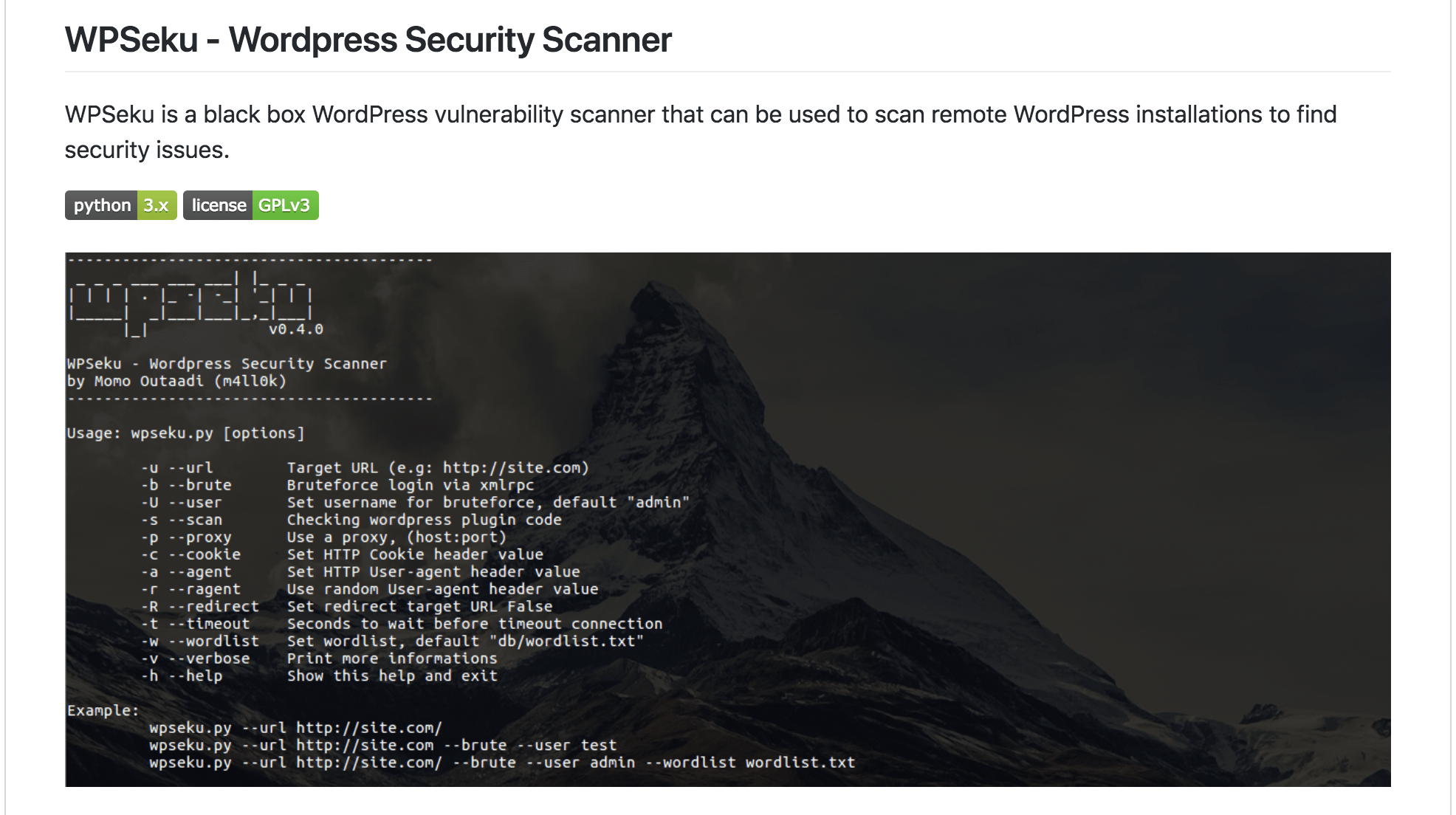
■WPSeku – WordPress Security Scanner
https://github.com/m4ll0k/WPSeku
WordPress脆弱性スキャナは、プラグイン/ログインパスワード/テーマ/wordpressのコード)を内部や外部で発見することができるOSS。WPSekuはWPScan Vulnerability Databaseを使ってパースしている模様。 言語はPythonでできてるみたい。早速自分のブログをスキャンしてやりました。
■Installation
基本ローカルにインストールしてURLでスキャンできますが、テーマやwordpress自体のコードもスキャンしたかったのでサーバ上に今回はインストールしています。
・git clone
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 |
$ git clone https://github.com/m4ll0k/WPSeku.git wpseku Cloning into 'wpseku'... remote: Enumerating objects: 2, done. remote: Counting objects: 100% (2/2), done. remote: Compressing objects: 100% (2/2), done. remote: Total 424 (delta 0), reused 1 (delta 0), pack-reused 422 Receiving objects: 100% (424/424), 898.17 KiB | 1.51 MiB/s, done. Resolving deltas: 100% (228/228), done. $ cd wpseku $ pip3 install -r requirements.txt Collecting requests (from -r requirements.txt (line 1)) Downloading https://files.pythonhosted.org/packages/65/47/7e02164a2a3db50ed6d8a6ab1d6d60b69c4c3fdf57a284257925dfc12bda/requests-2.19.1-py2.py3-none-any.whl (91kB) 100% |████████████████████████████████| 92kB 5.6MB/s Collecting urllib3 (from -r requirements.txt (line 2)) Downloading https://files.pythonhosted.org/packages/bd/c9/6fdd990019071a4a32a5e7cb78a1d92c53851ef4f56f62a3486e6a7d8ffb/urllib3-1.23-py2.py3-none-any.whl (133kB) 100% |████████████████████████████████| 143kB 7.0MB/s Collecting humanfriendly (from -r requirements.txt (line 3)) Downloading https://files.pythonhosted.org/packages/fb/34/1e80e4a06020f7dfc7eee11387e400435236f992f80eaa6ed9b3d8252211/humanfriendly-4.16.1-py2.py3-none-any.whl (71kB) 100% |████████████████████████████████| 81kB 6.7MB/s Collecting idna<2.8,>=2.5 (from requests->-r requirements.txt (line 1)) Downloading https://files.pythonhosted.org/packages/4b/2a/0276479a4b3caeb8a8c1af2f8e4355746a97fab05a372e4a2c6a6b876165/idna-2.7-py2.py3-none-any.whl (58kB) 100% |████████████████████████████████| 61kB 8.9MB/s Collecting certifi>=2017.4.17 (from requests->-r requirements.txt (line 1)) Downloading https://files.pythonhosted.org/packages/56/9d/1d02dd80bc4cd955f98980f28c5ee2200e1209292d5f9e9cc8d030d18655/certifi-2018.10.15-py2.py3-none-any.whl (146kB) 100% |████████████████████████████████| 153kB 7.6MB/s Collecting chardet<3.1.0,>=3.0.2 (from requests->-r requirements.txt (line 1)) Downloading https://files.pythonhosted.org/packages/bc/a9/01ffebfb562e4274b6487b4bb1ddec7ca55ec7510b22e4c51f14098443b8/chardet-3.0.4-py2.py3-none-any.whl (133kB) 100% |████████████████████████████████| 143kB 7.7MB/s Installing collected packages: idna, certifi, chardet, urllib3, requests, humanfriendly Successfully installed certifi-2018.10.15 chardet-3.0.4 humanfriendly-4.16.1 idna-2.7 requests-2.19.1 urllib3-1.23 |
■Usage
・Generic Scan blog.adachin.me
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 |
$ python3 wpseku.py --url https://blog.adachin.me --verbose ---------------------------------------- _ _ _ ___ ___ ___| |_ _ _ | | | | . |_ -| -_| '_| | | |_____| _|___|___|_,_|___| |_| v0.4.0 WPSeku - Wordpress Security Scanner by Momo Outaadi (m4ll0k) ---------------------------------------- [ + ] Target: https://blog.adachin.me [ + ] Starting: 11:04:30 [ + ] Server: h2o/2.2.5 [ + ] Uncommon header "x-powered-by" found, with contents: PHP/7.2.10-0ubuntu0.18.04.1 [ + ] Uncommon header "content-type" found, with contents: text/html; charset=UTF-8 [ + ] Uncommon header "vary" found, with contents: Accept-Encoding, Cookie [ + ] Uncommon header "cache-control" found, with contents: max-age=3, must-revalidate [ + ] Uncommon header "content-encoding" found, with contents: gzip [ i ] Checking Full Path Disclosure... [ i ] Checking wp-config backup file... [ + ] wp-config.php available at: https://blog.adachin.me/wp-config.php [ i ] Checking common files... [ + ] robots.txt file was found at: https://blog.adachin.me/robots.txt [ + ] sitemap.xml file was found at: https://blog.adachin.me/sitemap.xml [ + ] readme.html file was found at: https://blog.adachin.me/readme.html [ i ] Checking directory listing... [ i ] Checking wp-loging protection... [ i ] Checking robots paths... [ + ] Robots was found at: https://blog.adachin.me/robots.txt ---------------------------------------- Sitemap: https://blog.adachin.me/sitemap.xml Sitemap: https://blog.adachin.me/news-sitemap.xml User-agent: * Disallow: /wp-admin/ Allow: /wp-admin/admin-ajax.php ---------------------------------------- [ i ] Checking WordPress version... [ + ] Running WordPress version: 4.9.8 | Not found vulnerabilities [ i ] Passive enumeration themes... [ + ] Not found themes with passive enumeration [ i ] Passive enumeration plugins... [ + ] Name: social-media-widget [ i ] Checking plugins changelog... [ i ] Checking plugins full path disclosure... [ i ] Checking plugins license... [ i ] Checking plugins readme... [ i ] Checking plugins directory listing... [ i ] Checking plugin vulnerabilities... b'{"social-media-widget":{"latest_version":"4.0.6","last_updated":"2017-02-05T23:03:00.000Z","popular":true,"vulnerabilities":[{"id":6799,"title":"Social Media Widget - malicious code","created_at":"2014-08-01T10:58:59.000Z","updated_at":"2015-05-15T13:48:08.000Z","published_date":null,"references":{"url":["https://plugins.trac.wordpress.org/changeset?reponame=&old=691839@social-media-widget/trunk&new=693941@social-media-widget/trunk","http://slashdot.org/submission/2592777/top-wordpress-widget-sold-off-turned-into-seo-spambot"]},"vuln_type":"UNKNOWN","fixed_in":"4.0.2"},{"id":6800,"title":"Social Media Widget 4.0 - social-widget.php MITM Weakness Arbitrary Code Injection","created_at":"2014-08-01T10:58:59.000Z","updated_at":"2015-05-15T13:48:08.000Z","published_date":null,"references":{"url":["http://seclists.org/oss-sec/2013/q2/10"],"cve":["2013-1949"],"secunia":["53020"]},"vuln_type":"UNKNOWN","fixed_in":"4.0.1"}]}}' | Not found vulnerabilities [ i ] Enumerating users... ------------------------------- | ID | Username | Login | ------------------------------- | 0 | あだちん | haha-bakame | | 1 | あだちん | None | | 2 | h | | ------------------------------- |
とりあえず脆弱性はなさそう!!セキュア!
ログインユーザーもわかりますな。(偽装してます)
・Scan plugin,theme and wordpress code
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 |
$ sudo python3 wpseku.py --scan /var/www/wordpress --verbose ---------------------------------------- _ _ _ ___ ___ ___| |_ _ _ | | | | . |_ -| -_| '_| | | |_____| _|___|___|_,_|___| |_| v0.4.0 WPSeku - Wordpress Security Scanner by Momo Outaadi (m4ll0k) ---------------------------------------- [ + ] Checking PHP code... [ + ] Scanning directory... [ i ] Scanning /var/www/wordpress/wp-comments-post.php file [ + ] Not found vulnerabilities [ i ] Scanning /var/www/wordpress/xmlrpc.php file [ + ] Not found vulnerabilities [ i ] Scanning /var/www/wordpress/wp-cron.php file [ + ] Not found vulnerabilities [ i ] Scanning /var/www/wordpress/wp-trackback.php file --------------------------------------------------------------- | Line | Possibile Vuln. | String | --------------------------------------------------------------- | 88 | Open Redirect | wp_redirect(get_permalink($tb_id)) | --------------------------------------------------------------- [ i ] Scanning /var/www/wordpress/wp-settings.php file [ + ] Not found vulnerabilities [ i ] Scanning /var/www/wordpress/wp-activate.php file [ + ] Not found vulnerabilities [ i ] Scanning /var/www/wordpress/wp-config-sample.php file [ + ] Not found vulnerabilities [ i ] Scanning /var/www/wordpress/index.php file [ + ] Not found vulnerabilities [ i ] Scanning /var/www/wordpress/wp-login.php file ~省略~ |
ドキュメントルート配下全てスキャンされました。(長いので省略)
他にもパスワード辞書を使って、Bruteforce Loginチェックもできます。(激アツかよ)
■まとめ
非常に面白い!このスキャン結果をslackに通知できるようになったら良さそう。
その前に神戸さんVulsでちゃちゃっと作りそう。
ちなみにBruteforce Login scanはDDoS並みにアタックするので皆さん気をつけましょうw
みなさんもお試しあれ!



2件のコメント
マツ · 2019/10/08 3:24 pm
こちらのブログを参考にWPsekuを使ってみました^^
無事使えたのですが、どういう記述になると良くて、悪いのかが分からずで・・笑
問題点があったら文字色が変わる、という事はないですよね?・・
adachin · 2019/10/16 10:12 am
Not found vulnerabilitiesであれば問題ないので、それ以外は対応しないとまずいですね!